Spring Security: Authorization
In Spring Security, authorization is a process of granting or denying access to a resource. After a user has been authenticated, they may or may not be authorized to perform a given action. For example, a user may be authenticated with a username and password but not have the authority to view a resource because they don’t have the correct role.
Basics
The most basic way to authorize access to a resource is to define a authorization rule after the request matcher.
More about request matchers can be found Spring Security: Request Matching.
For instance, if we want to allow only users with the ADMIN role to access the /admin endpoint, we can do it like this:
@Beanpublic SecurityFilterChain filterChain(HttpSecurity http) throws Exception {http.authorizeHttpRequests(authorize -> authorize.anyRequest().authenticated().requestMatchers(HttpMethod.GET, "/admin").hasRole("ADMIN")).httpBasic(withDefaults());return http.build();}
AuthorizedUrl
requestMatchers method returns a AuthorizedUrl object from AuthorizeHttpRequestsConfigurer which , as the documentation says is:
An object that allows configuring the AuthorizationManager for RequestMatchers.
This class has couple of methods that can be used to define authorization rules. Some of the most popular are:
hasRole- only users with the specified role can access the resourcehasAuthority- only users with the specified authority can access the resourceaccess- allows to define a custom authorization ruleauthenticated- only authenticated users can access the resourcepermitAll- all users can access the resourcedenyAll- no users can access the resourceanonymous- only anonymous users can access the resource
Authorization Manager
Let’s dive into the details of the autorization process.
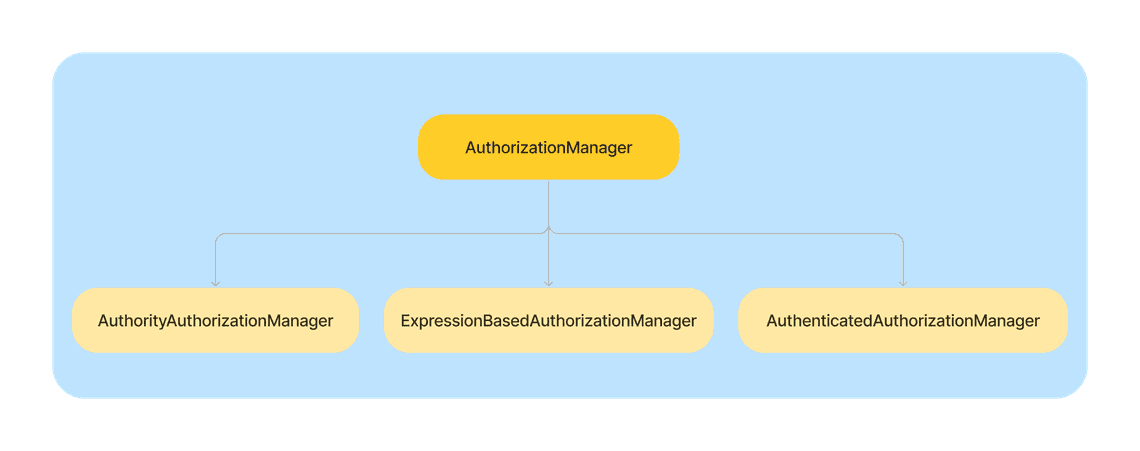
When you use any of the methods of the AuthorizedUrl class, you are using an instance of the AuthorizationManager.
For example, when you use hasAuthority method, you are using an instance of the AuthorityAuthorizationManager class from Spring Security.
Here are some of the most popular authorization managers:
Custom Authorization
In order to define a custom authorization rules, we need to define a class that implements a AuthorizationManager interface:
public class CustomAuthorizationManager implements AuthorizationManager<RequestAuthorizationContext> {@Overridepublic AuthorizationDecision check(Supplier<Authentication> authentication,RequestAuthorizationContext object) {return new AuthorizationDecision(authentication.get().getPrincipal().equals("admin"));}}
This class will only allow access to the resource if the principal is equal to admin.
Then, we can provide an instance of this class to the access method of the HttpSecurity object, right after request matcher:
@Beanpublic SecurityFilterChain filterChain(HttpSecurity http) throws Exception {http.authorizeHttpRequests(authorize -> authorize.anyRequest().authenticated().requestMatchers(HttpMethod.GET, "/admin").access(new CustomAuthorizationManager())).httpBasic(withDefaults());return http.build();}
Conclusion
- Authorization is a process of granting or denying access to a resource.
- In Spring Security, authorization is done by defining authorization rules after the request matcher.
- We always define the authorization by providing some instance of the
AuthorizationManagerinterface. - Spring Security provides many authorization managers out of the box, like
AuthorityAuthorizationManager. - You can define your own authorization manager by implementing the
AuthorizationManagerinterface.
Quick Links
Legal Stuff